In this chapter we are going to discuss about an interesting system combining symmetric cryptography and asymmetric cryptography using pros of each of them.
Protocol
Security over the Web is implemented through HTTPS protocol. This protocol in turn use another protocol called TLS which is actually the one in charge of providing the security.
How does it work ?
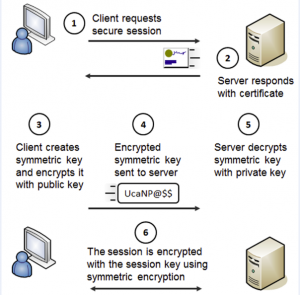
TLS is a complex protocol embracing itself several sub-protocols. We are going to briefly see the two main phases performed by TLS. Figure 7.1 provides an overview on how TLS does work.
- The user enters an URL using HTTPS in his web browser, for example https://www.wikipedia.org/.
- Server sends to user’s computer his digital certificate.
- The web browser checks if the concerned certificate authority is trustworthy against its internally list as well as the digital certificate integrity. In case everything is fine the web browser generates a key called session key.
- The session key is encrypted by using server’s public key and sent to it.
- Server decrypts the message from the user’s computer with his private key and gets the session key.
- Finally, the actual communication starts. From now on communications are encrypted and decrypted with the session key using symmetric cryptography. The symmetric encryption algorithm results from a negotiation between the web browser and the server happened previously.
Standard
TLS is the continuation of SSL. TLS is a IETF standardard since 2001. Many patches were done following the discovered weaknesses of TLS over the time (BREACH, BEAST, CRIME, TIME, Lucky 13, POODLE, etc.). Yet the way TLS combines symmetric and asymmetric cryptography makes it flexible and efficient.
Limitation
The security of the system as a whole showed its limitation when some certification authorities were compromised in the past (Comodo, DigiNotar, Turktrust).
Following those compromises, some web browsers now restrict the trust accorded to certification authorities by checking if a certificate sent by a web site is the expected one. This technique is known under certificate pinning.