Asymmetric cryptography originates with the research work of Whitfield Diffie and Martin Hellman. The paper they published in 1976 completely revolutionized cryptography. The algorithm they designed avoids communicants to agree upon a shared key beforehand and thus solved the so-called key distribution problem encountered with symmetric cryptography.
1. Principle
Asymmetric cryptography (or public-key cryptography) has been called that way since the key for encrypting differs from the key for decrypting the ciphertext. In asymmetric cryptography each entity owns two keys, the public key and the private key. The public key, as its name suggests, can be known by everyone and thus be published in a directory or on a web site. The private key is secret. Both are mathematically tied, but it is very difficult to deduce the secret key knowing the public one because the computation time is way too long.
2. Illustration
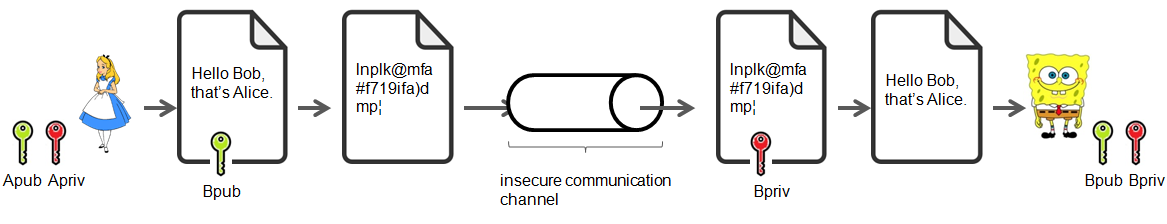
Figure 3.1 illustrates how asymmetric encryption works in general. Let’s imagine that Alice and Bob would like to have privacy communication over an insecure channel, for instance internet. Alice goes to Bob’s web page, which is available to anyone and contains his public key. She then encrypts the message she’d like to send to Bob by using his key that she obtained beforehand. Then Alice sends the encrypted message to Bob by email. Upon receipt of the email, Bob can decrypt the message – only he can do it – by using his private key. Alice and Bob must of course agree upon the encryption algorithm they want to use.
3. Main drawback
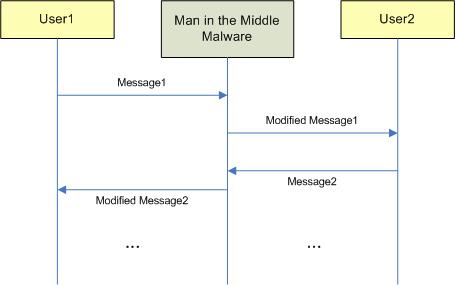
Asymmetric cryptography is vulnerable to the so-called man-in-the-middle attack (MITM). Let’s describe the steps of this attack over the time.
-
Alice wants to know Bob’s public key. On that purpose, she sends him the following email.
Hi Bob, please give me your public key. Alice. - MITM captures the message. MITM simply relays Alice’s message to Bob.
-
Bob gets the message. He does believe that the message comes from Alice directly and replies the following.
Hi Alice. Here you are. My public key is 40UmQ3B3Ku. Bob. -
MITM gets Bob’s message. MITM replaces Bob’s public key by his own and sends Alice the following altered message.
Hi Alice. Here you are. My public key is FdMY0LBX41. Bob. -
Alice gets MITM’s message. She does believe that the message comes from Bob directly and replies the following.
Bob, I have a crush on you ! Alice.
She then encrypts it using MITM’s public key and sends the ciphertext to Bob. -
Again MITM captures Alice’s message. MITM can decrypt it with his private key. He also can modify it such as the following.
Bob, you are not the kind of guy I am keen on ! Alice.
MITM can then encrypt it by using Bob’s public key he got previously and send it to Bob, and so on.
Figure 3.2 illustrates the MITM attack over the time. In this attack, a third party (most of the time a computer program) hijacks communication and impersonates the other party.
We will see later on how the digital certificate addresses this issue.
5. Popular ciphers
RSA and El Gamal are widely used asymmetric encryption algorithms.