1. Goal
The goal of the digital certificate is to officially associate an entity with its public key. This therefore solves the problem of the MITM which we discussed.
The concept of the digital certificate was introduced in 1978 by Loren Kohnfelder in his Bachelor thesis at MIT under the supervision of Leonard Adleman.
2. Principle
The idea is to involve a trusted third party for guarantying that a public key is well associated with a given entity. This trusted third party is called the certification authority (AC) and its role is thus to certify that a given entity (corporation, server, physical person) possesses a given public key. The certification authority performs the necessary checks before actually issuing the certificate.
There are plenty of AC’s on the market. Verisign, Thawte, GeoTrust, Digicert, Let’s Encrypt (free) are some of the players on this market.
3. Public document
There is a strong misconception about digital certificate. Quite often it is reported in the media that digital certificates has been stolen allowing to some hackers to commit whatever fraudulent operation. This must be very clear : a digital certificate is by definition a public document. It does not make any sense talking about the theft of a digital certificate.
4. Illustration
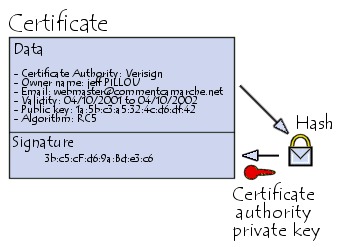
Figure 5.1 illustrates a digital certificate. It contains among other information the name of entity, the name of issuing AC, the validity period and of course the public key.
Certificate is digitally signed by the issuing AC. Certification authorities indeed possess as well a public key/private key pair. The signature allows to verify the integrity of the certificate (p.ex. public key alteration), as we seen in the dedicated chapter.
5. Usage
Before actually starting with a communication, parties exchange their certificate each other.
Then, each party checks the integrity of the certificate. For doing that, each compares the hash mentioned in the certificate with the hash that has been computed on its own, as we seen previously.
6. Intermediary AC
Corporations having plenty of domain names won’t buy a digital certificate each time they acquire a new domain name. Those one in fact manage their own AC.
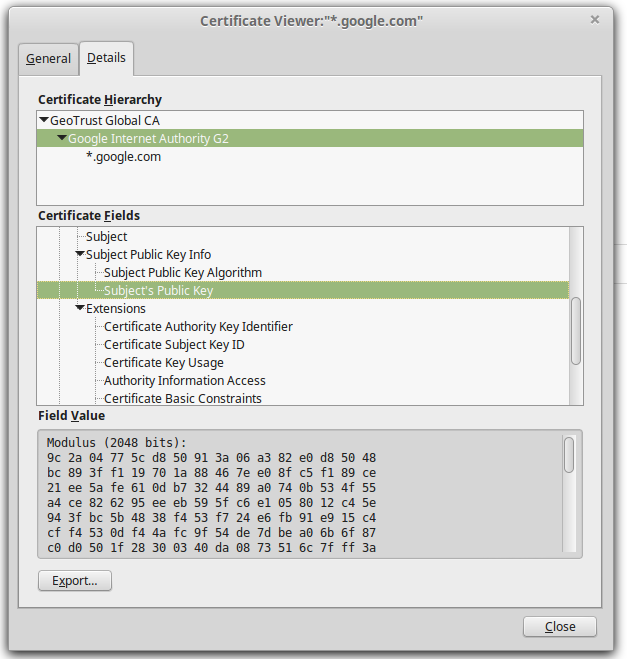
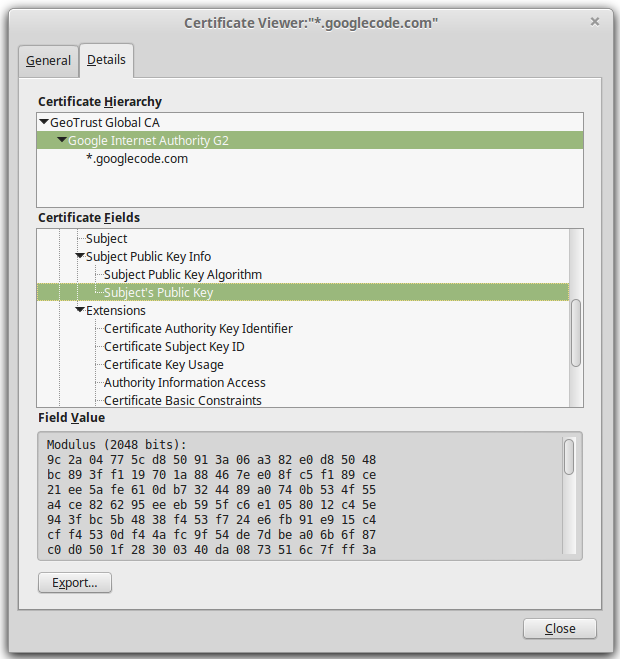
As an example, the intermediary AC Google Internet Authority G2 digitally sign the certificates for the domain names *.google.com (Figure 5.2) as well as *.googlecode.com (Figure 5.3).