1. Goal
The digital signature fulfills a dual role. First it provides information on if modifications were made or not to a message during its transportation. This feature is called the integrity of a message. Second, the identity of the sender can be verified. That feature is called the authentication.
2. Hash
Before actually covering the digital signature, let’s first discuss about the hash which is an independent concept.
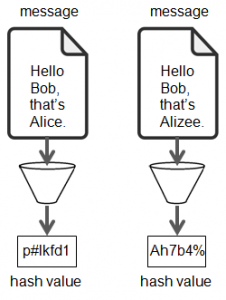
A hash is a digest or a summary of a given information (e.g. text or document). To get the hash, the information is applied as an input to a mathematical function. That function is called hash function and its output is called the hash (see Figure 4.1).
As an example, let’s apply the following text Hello Bob, that's Alice. to whatever hashing function $f$. We get the hash as follows :
$$f(\text{Hello Bob, that’s Alice.})=\text{p#lkfd1}$$
A hashing function has several mathematical properties. We here just mention that a hashing function is one-way function. It means that knowing both the output and the hashing function, it’s impossible to get the input back.
MD5 (no longer secure) and SHA-3 are popular hashing functions just to name a few.
3. Digital signature = encrypted hash
To the original message a hash of it is added. That hash is encrypted by using the private key of the sender. This constitutes the digital signature.
4. Illustration
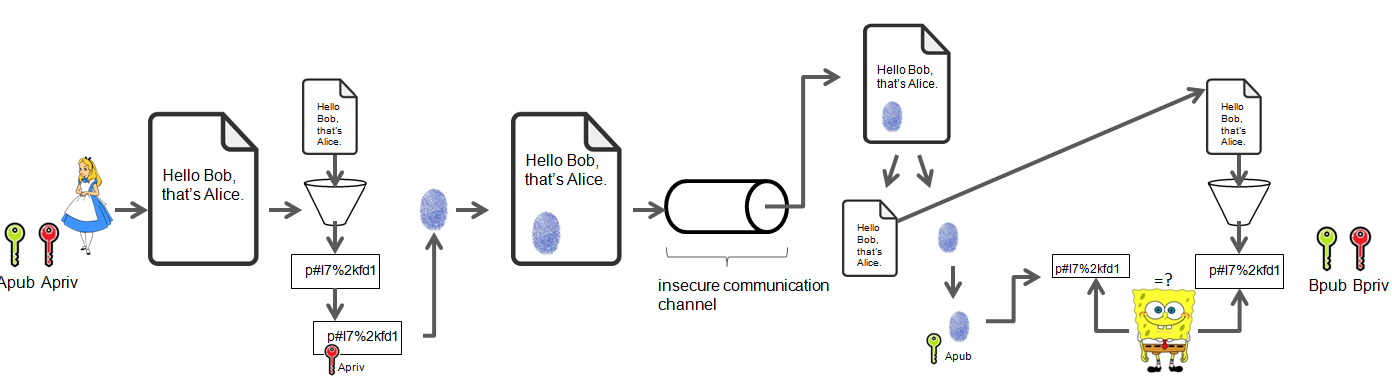
- Alice writes to Bob the following message :
Hello Bob, that's Alice.. She applies it to a hash function and gets the hash. Then she encrypts the hash with her private key. Finally, she attaches the encrypted hash (signature) to the message and send the whole thing to Bob. - Upon receipt Bob separates message and signature from each other. He decrypts the digital signature by using Alice’s public key. He then applies the message to the hash function. He gets another hash and compares them with each other. If both are same it means that the original message has not been modified along the way. Obviously, Bob has to use the same encryption algorithm as well as the same hash function that Alice did.
Digital signature thus provides :
- Integrity : If the original message is modified during the transportation, the hashs won’t be the same.
- Authentication : If the signature is falsified during the transportation, the hashs won’t be the same.
6. Main drawback
Now suppose that we encrypt the whole thing (message + digital signature) with the public key of the recipient and send it to the recipient, as we discussed in the chapter dedicated to asymmetric cryptography. The recipient can decrypt the whole thing with his private key and can check if the hash values are the same.
However, the problem of the MITM attack still remains. By hijacking the communication in both ways as discussed, MITN still can decrypt messages. The digital certificate definitely solves this problem.