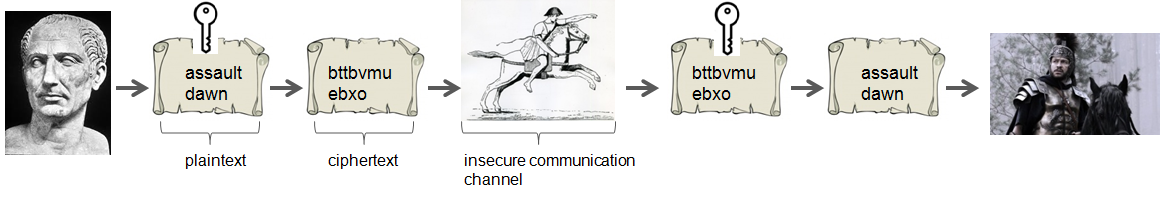
In order to illustrate how symmetric cryptography works in general, let’s pick a very simple cipher, the so-called Caesar cipher. It has been invented by Jules Caesar for keeping privacy in his diplomatic and military communications.
1. Illustration: Caesar chipher
Figure 2.1 depicts the process of encrypting the plaintext : assault dawn. The Caesar cipher operates as follows : each letter of the message is replaced by the letter corresponding to a shift further down in the alphabet. Thus a becomes b, b becomes b, and so on. The resulting ciphertext is bttbvmu ebxo. The decryption operates the other way around, namely by shifting one letter up in the alphabet. In the present case the key equals to the number of shift in the alphabet, means 1.
The Caesar cipher shows how symmetric cryptography operates. Encryption and decryption both use the same key, hence the name. The Caesar cipher is pretty insecure. It can indeed easily be broken using statistical methods. However at that time few people could read. The writing itself provided an encryption system.
2. Main drawback
Symmetric cryptography has an important issue. Obviously the parties have to agree upon a common key to use before starting to exchange encrypted messages. However that key must anyway be communicated in a secure way ! We are getting into a snake biting its own tail situation, which is called the key distribution problem.
We will see how asymmetric cryptography addresses this issue.
4. Popular ciphers
Blowfish, IDEA, AES, DES, just to name a few, are complex and widely used symmetric ciphers.